Sophos also allows security admins to manage all Sophos products from a single, cloud-based console. Sophos provides different methods for automating the deployment of software to Windows computers. SCCM makes it easier to deploy Sophos central installer to multiple window computers. This knowledge base article provides a high-level overview on how to use Microsoft Intune to deploy the Sophos Central Windows endpoint software. The following information could also be used as a guide when deploying the Sophos. Sophos connects to Intune and requires you to sign in to your Intune subscription. In the Microsoft Intune authentication window, enter your Intune credentials and Accept the permissions request for Sophos Mobile Thread Defense. On the Sophos setup page, select Save to complete the configuration for Intune.
- Sophos Intune Mac
- Sophos Intune Install
- Uninstall Sophos Intune
- Sophos Intune Download
- Sophos Intune
- Sophos Intune Integration
This knowledge base article provides a high-level overview on how to use Microsoft Intune to deploy the Sophos Central Windows endpoint software. The following information could also be used as a guide when deploying the Sophos Enterprise Console (SEC) managed client.
Complete the following steps to integrate the Sophos Mobile Threat Defense solution with Intune.
Note
This Mobile Threat Defense vendor is not supported for unenrolled devices.
Before you begin
Before starting the process of integrating Sophos Mobile with Intune, make sure you have the following:
- Microsoft Intune subscription
- Azure Active Directory admin credentials to grant the following permissions:
- Sign in and read user profile
- Access the directory as the signed-in user
- Read directory data
- Send device information to Intune
- Admin credentials to access the Sophos Mobile admin console.
Sophos Mobile app authorization
The Sophos Mobile app authorization process follows:
- Allow the Sophos Mobile service to communicate information related to device health state back to Intune.
- Sophos Mobile syncs with Azure AD Enrollment Group membership to populate its device's database.
- Allow the Sophos Mobile admin console to use Azure AD Single Sign On (SSO).
- Allow the Sophos Mobile app to sign in using Azure AD SSO.
To set up Sophos Mobile integration
Sign in to the Microsoft Endpoint Manager admin center portal, go to Tenant administration > Connectors and tokens > Mobile Threat Defense > and select Add.
On the Add Connector page, use the dropdown and select Sophos. And then select Create.
Select the link Open the Sophos admin console.
Sign in to the Sophos admin console with your Sophos credentials.
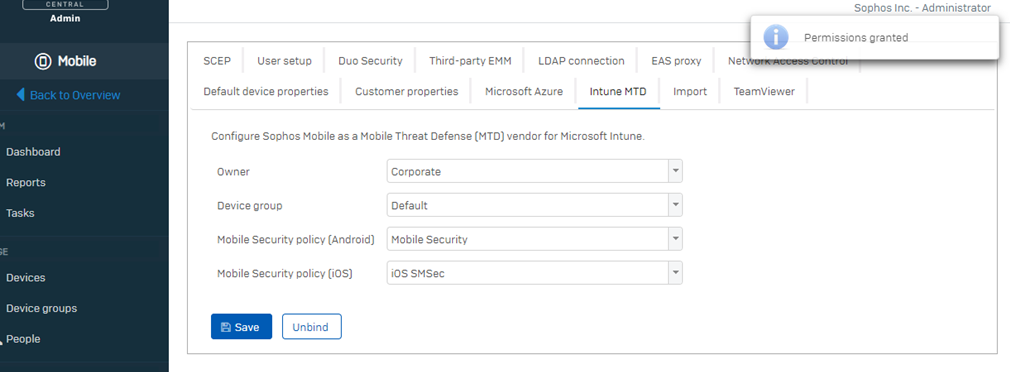
Go to Mobile > Settings > Setup > Sophos setup.
On the Sophos setup page, select the Intune MTD tab.
Select Bind, and then select Yes. Sophos connects to Intune and requires you to sign in to your Intune subscription.
In the Microsoft Intune authentication window, enter your Intune credentials and Accept the permissions request for Sophos Mobile Thread Defense.
On the Sophos setup page, select Save to complete the configuration for Intune:
When the message Successful Integration appears, integration is complete.
In the Intune console, Sophos is now available.
Next Steps
-->You can use Intune to add and deploy Mobile Threat Defense (MTD) apps so that end users can receive notifications when a threat is identified in their mobile devices, and to receive guidance to remediate the threats.
Note
This article applies to all Mobile Threat Defense partners.
Before you begin
Complete the following steps in Intune. Make sure you're familiar with the process of:
- Adding an app into Intune.
- Adding an iOS app configuration policy into Intune.
- Assigning an app with Intune.
Tip
The Intune Company Portal works as the broker on Android devices so users can have their identities checked by Azure AD.
Configure Microsoft Authenticator for iOS
For iOS devices, you need the Microsoft Authenticator so users can have their identities checked by Azure AD. Additionally, you need an iOS app configuration policy that sets the MTD iOS app you use with Intune.
See the instructions for adding iOS store apps to Microsoft Intune. Use this Microsoft Authenticator app store URL when you configure App information.
Configure your MTD apps with an app configuration policy
To simplify user onboarding, the Mobile Threat Defense apps on MDM-managed devices use app configuration. For unenrolled devices, MDM based app configuration is not available, so please refer to Add Mobile Threat Defense apps to unenrolled devices.
Better Mobile app configuration policy
Sophos Intune Mac
See the instructions for using Microsoft Intune app configuration policies for iOS to add the Better Mobile iOS app configuration policy.
For Configuration settings format, select Enter XML data, copy the following content and paste it into the configuration policy body. Replace the
https://client.bmobi.netURL with the appropriate console URL.
Check Point SandBlast Mobile app configuration policy
See the instructions for using Microsoft Intune app configuration policies for iOS to add the Check Point SandBlast Mobile iOS app configuration policy.
For Configuration settings format, select Enter XML data, copy the following content and paste it into the configuration policy body.
<dict><key>MDM</key><string>INTUNE</string></dict>
Lookout for Work app configuration policy
Create the iOS app configuration policy as described in the using iOS app configuration policy article.
MVISION Mobile app configuration policy
Android Enterprise
See the instructions for using Microsoft Intune app configuration policies for Android to add the MVISION Android app configuration policy.
For Configuration settings format, select Use configuration designer, and add the following settings:
| Configuration key | Value type | Configuration value |
|---|---|---|
| MDMDeviceID | string | {{AzureADDeviceId}} |
| tenantid | string | Copy value from admin console “Manage” page in the MVISION console |
| defaultchannel | string | Copy value from admin console “Manage” page in the MVISION console |
iOS
See the instructions for using Microsoft Intune app configuration policies for iOS to add the MVISION Mobile iOS app configuration policy.
For Configuration settings format, select Use configuration designer, and add the following settings:

| Configuration key | Value type | Configuration value |
|---|---|---|
| MDMDeviceID | string | {{AzureADDeviceId}} |
| tenantid | string | Copy value from admin console “Manage” page in the MVISION console |
| defaultchannel | string | Copy value from admin console “Manage” page in the MVISION console |
Pradeo app configuration policy
Pradeo doesn't support application configuration policy on iOS/iPadOS. Instead, to get a configured app, work with Pradeo to implement custom IPA or APK files that are preconfigured with the settings you want.
SEP Mobile app configuration policy
Use the same Azure AD account previously configured in the Symantec Endpoint Protection Management console, which should be the same account used to sign in to the Intune.
- Download the iOS app configuration policy file:
Go to Symantec Endpoint Protection Management console and sign in with your admin credentials.
Go to Settings, and under Integrations, choose Intune. Choose EMM Integration Selection. Choose Microsoft, and then save your selection.
Click the Integration setup files link and save the generated *.zip file. The .zip file contains the *.plist file that will be used to create the iOS app configuration policy in Intune.
See the instructions for using Microsoft Intune app configuration policies for iOS to add the SEP Mobile iOS app configuration policy.
- For Configuration settings format, select Enter XML data, copy the content from the *.plist file, and paste its content into the configuration policy body.
Note
If you are unable to retrieve the files, contact Symantec Endpoint Protection Mobile Enterprise Support.
Sophos Mobile app configuration policy
Create the iOS app configuration policy as described in the using iOS app configuration policy article. For additional information, see Sophos Intercept X for Mobile iOS - Available managed settings in the Sophos knowledge base.
Wandera app configuration policy
Note
For initial testing, use a test group when assigning users and devices in the Assignments section of the configuration policy.
Android Enterprise
See the instructions for using Microsoft Intune app configuration policies for Android to add the Wandera Android app configuration policy using the information below when prompted.
Sophos Intune Install
- In the RADAR Wandera Portal, click the Add button under Configuration settings format.
- Select Activation Profile URL from the list of Configuration Keys. Click OK.
- For Activation Profile URL select string from the Value type menu then copy the Shareable Link URL from the desired Activation Profile in RADAR.
- In the Intune admin console app configuration UI, select Settings, define Configuration settings format > Use Configuration Designer and paste the Shareable Link URL.
Note
Unlike iOS, you will need to define a unique Android Enterprise app configuration policy for each Wandera Activation Profile. If you don’t require multiple Wandera Activation Profiles, you may use a single Android app configuration for all target devices. When creating Activation Profiles in Wandera, be sure to select “Azure Active Directory” under the Associated User configuration to ensure Wandera is able to synchronize the device with Intune via UEM Connect.
iOS
See the instructions for using Microsoft Intune app configuration policies for iOS to add the Wandera iOS app configuration policy using the information below when prompted.
- In RADAR Wandera Portal, navigate to Devices > Activations and select any activation profile. Click Deployment Strategies > Managed Devices > Microsoft Intune and locate the iOS App Configuration settings.
- Expand the box to reveal the iOS app configuration XML and copy it to your system clipboard.
- In Intune admin console app configuration UI Settings, define Configuration settings format > Enter XML data.
- Paste the XML in the app configuration text box.
Note
A single iOS configuration policy may be used across all devices that are to be provisioned with Wandera.
Zimperium app configuration policy
Android Enterprise
See the instructions for using Microsoft Intune app configuration policies for Android to add the Zimperium Android app configuration policy.
For Configuration settings format, select Use configuration designer, and add the following settings:
| Configuration key | Value type | Configuration value |
|---|---|---|
| MDMDeviceID | string | {{AzureADDeviceId}} |
| tenantid | string | Copy value from admin console “Manage” page in the Zimperium console |
| defaultchannel | string | Copy value from admin console “Manage” page in the Zimperium console |
iOS
See the instructions for using Microsoft Intune app configuration policies for iOS to add the Zimperium iOS app configuration policy.
For Configuration settings format, select Use configuration designer, and add the following settings:
| Configuration key | Value type | Configuration value |
|---|---|---|
| MDMDeviceID | string | {{AzureADDeviceId}} |
| tenantid | string | Copy value from admin console “Manage” page in the Zimperium console |
| defaultchannel | string | Copy value from admin console “Manage” page in the Zimperium console |
Assigning Mobile Threat Defense apps to end users via Intune
To install the Mobile Threat Defense app on the end user device, you can follow the steps that are detailed in the following sections. Make sure you're familiar with the process of:
Choose the section that corresponds to your MTD provider:
Assigning Better Mobile
Uninstall Sophos Intune
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Active Shield app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this ActiveShield app store URL for the Appstore URL.
Assigning Check Point SandBlast Mobile
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Check Point SandBlast Mobile app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this Check Point SandBlast Mobile app store URL for the Appstore URL.
Assigning Lookout for Work
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Lookout for work Google app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this Lookout for Work iOS app store URL for the Appstore URL.
Lookout for Work app outside the Apple store
You must re-sign the Lookout for Work iOS app. Lookout distributes its Lookout for Work iOS app outside of the iOS App Store. Before distributing the app, you must re-sign the app with your iOS Enterprise Developer Certificate.
For detailed instructions to re-sign the Lookout for Work iOS apps, see Lookout for Work iOS app re-signing process on the Lookout website.
Enable Azure AD authentication for Lookout for Work iOS app users.
Go to the Azure portal, sign in with your credentials, then navigate to the application page.
Add the Lookout for Work iOS app as a native client application.
Replace the com.lookout.enterprise.yourcompanyname with the customer bundle ID you selected when you signed the IPA.
Add additional redirect URI: <companyportal://code/> followed by a URL encoded version of your original redirect URI.
Add Delegated Permissions to your app.
Note
See configure a native client application with Azure AD for more details.
Add the Lookout for Work ipa file.
- Upload the re-signed .ipa file as described in the Add iOS LOB apps with Intune article. You also need to set the minimum OS version to iOS 8.0 or later.
Assigning MVISION Mobile
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this MVISION Mobile app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this MVISION Mobile app store URL for the Appstore URL.
Assigning Pradeo
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Pradeo app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this Pradeo app store URL for the Appstore URL.
Assigning Sophos
Sophos Intune Download
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Sophos app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this ActiveShield app store URL for the Appstore URL.
Assigning Symantec Endpoint Protection Mobile
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this SEP Mobile app store URL for the Appstore URL. For Minimum operating system, select Android 4.0 (Ice Cream Sandwich).
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this SEP Mobile app store URL for the Appstore URL.
Assigning Wandera
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Wandera Mobile app store URL for the Appstore URL. For Minimum operating system, select Android 6.0.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this Wandera Mobile app store URL for the Appstore URL.
Assigning Zimperium
Sophos Intune
Android
- See the instructions for adding Android store apps to Microsoft Intune. Use this Zimperium app store URL for the Appstore URL.
iOS
- See the instructions for adding iOS store apps to Microsoft Intune. Use this Zimperium app store URL for the Appstore URL.
Sophos Intune Integration
Next steps
